Methods and Fake Wall Attacks Under SNI Review
Introduction to Some Professional Terms
HTTP(Hyper Text Transfer Protocol)
Hypertext Transfer Protocol, used for transmitting various web pages in daily browsing, but its transmission process is not encrypted and thus insecure.
What is currently referred to as supporting HTTP generally means that both HTTP and HTTPS functions can be implemented, rather than just HTTP alone.
TLS(Transport Layer Security)
Transport Layer Security, the successor to SSL, enables messages to be encrypted before being handed over to TCP for transmission. In other words, HTTP + TLS = HTTPS.
SNI(Server Name Indication)
Server Name Indication. SNI is an extension designed to address the issue of a single server using multiple domain names and certificates in SSL/TLS. It allows a server to support multiple certificates on the same IP address and TCP port, enabling multiple HTTPS or other TLS-based services to be requested on the same IP address.
In simple terms, it is a method for deploying different certificates on the same port of a server. The server processes the corresponding request based on the SNI domain name received in the request. If the SNI domain name is empty, it handles the request using a pre-set default domain name.
CDN(Content Delivery Network)
Content Delivery Network, a high-speed network topology formed by servers deployed in various regions, allowing users in each region to achieve fast access. CDN responds to different websites via SNI and also protects the security of root servers.
Nginx
A mainstream high-performance open-source HTTP reverse proxy tool, mainly used for reverse proxy, load balancing, and separation of dynamic and static resources.
Reverse Proxy
Deploying an outer server as a gateway in front of the root server, so that users can only access the outer server, thereby protecting the internal network server from exposure. As a gateway, it can also analyze and modify messages.
Proxy servers and root servers deployed on the same host are called local reverse proxies.
Current Mainstream Blocking Technologies
Here is a brief overview of the technologies; for more details, please search on your own Baidu it.
In current life, GFW blocks prohibited websites mainly through two methods: 1. DNS pollution, 2. TCP reset attacks.
DNS Pollution
This primarily involves checking keywords in HTTP messages to intercept content from the corresponding websites, resulting in a ERR_CONNECTION_TIMED_OUT error in the browser, as DNS is directed to an inaccessible address, causing the access to time out. DNS queries can reach the DNS server, but if they match prohibited keywords, the firewall will inject a false DNS response before the legitimate DNS response. The solution to this issue is to perform local resolution by modifying the local Hosts file to connect directly via IP.
However, in current life, the use of DNS pollution for blocking large websites has become rare, mainly because HTTPS encrypts the browsing content, making keyword detection in messages ineffective.
SNI Review Method
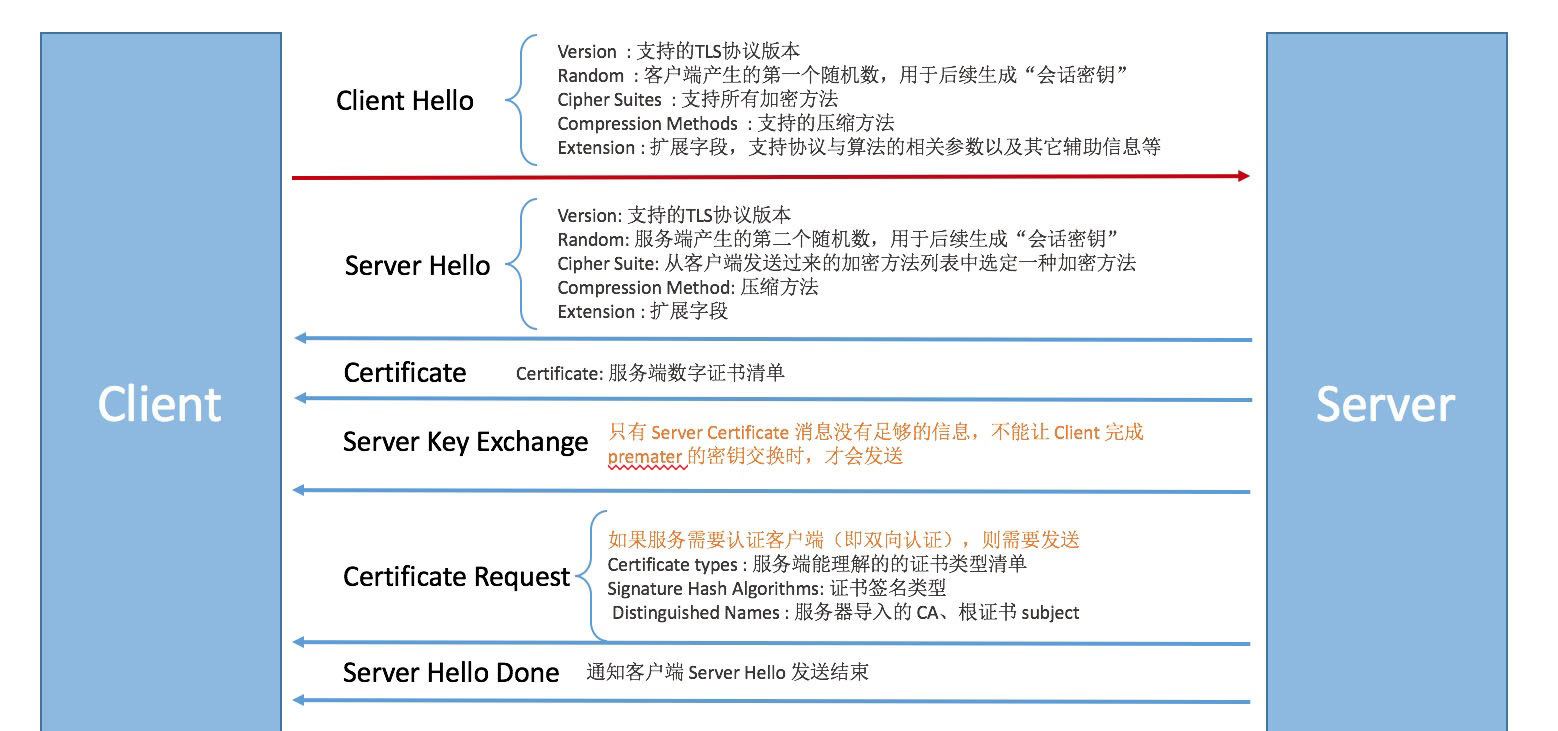
Under normal circumstances, the TLS handshake requires the following stages:
At the initial Client Hello stage, both parties have not yet agreed on the encryption method, so the message is in plaintext, and the Extension field contains the SNI information, which is the domain name currently being requested, and this information can be obtained through packet capture.
In normal situations, the server responds with the corresponding domain certificate based on the domain name in SNI and proceeds with the subsequent handshake steps. After negotiation, encrypted communication begins.
However, during this process, GFW can intercept the domain name in SNI to determine the legitimacy of the website the client is requesting and perform detection and blocking. The blocking method is TCP reset attacks. This technique is known as SNI blocking based on deep packet inspection.
TCP reset attacks are executed using a single packet. The attacker creates and sends a forged TCP reset packet to interfere with the connection between the user and the website, deceiving both parties into terminating the TCP connection.
Currently, GFW sends RST messages preemptively to interrupt such connections. This technology is also known as TCP keyword blocking.
A Feasible Solution
SNI is a method for deploying different certificates on the same port of a server. The well-known Cloudflare provides certificates based on SNI after enabling CDN. An important process in implementing SNI is sending the domain name to be connected when establishing a connection between the client and server, so that the server can return a certificate issued for the specified domain name.
In this process, if the user requests a non-existent domain name, the server will send a default certificate to the client to allow the connection to continue.
The method of bypassing blocking by obfuscating the Server Name is called Domain Fronting. In simple terms, it involves not carrying SNI or carrying an invalid SNI in the Client Hello stage to hide the real connection website and evade internet censorship.
This is currently effective for large websites such as Steam, Pixiv, and Github.
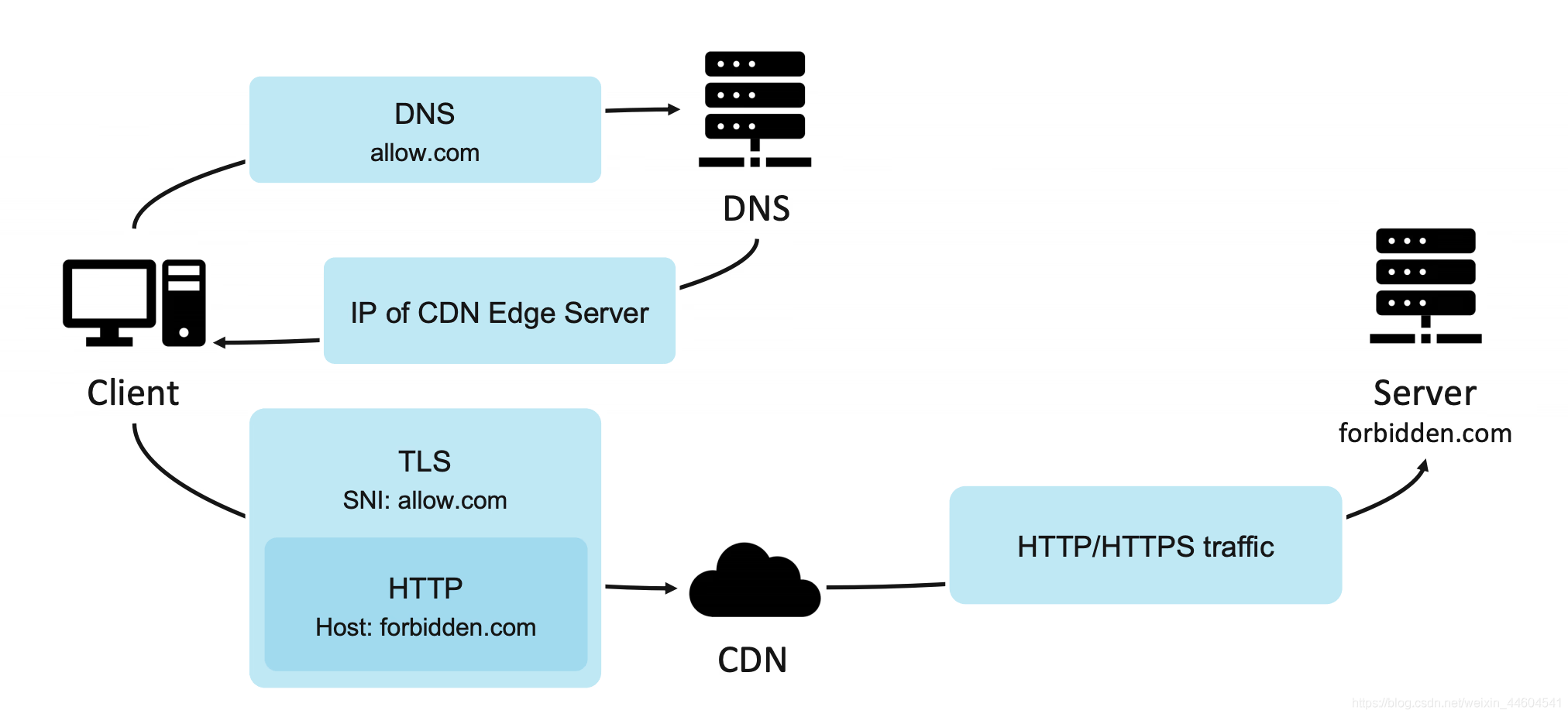
How Domain Fronting Works
Users use a legitimate domain name to request the CDN’s IP from DNS, then initiate a request to the CDN. When processing HTTPS requests, the CDN first decrypts it and forwards the request based on the HTTP Host value. Therefore, users wanting to access an illegal website can use a legitimate domain name on the CDN as the SNI, and then use it as the HTTP Host for HTTPS communication with the CDN. Since the HTTP Host can only be seen by the forwarder and not by the censor, the CDN will allow this request and re-encapsulate the HTTP request based on the HTTP Host, sending it to the actual requested server. In this case, the client is actually communicating with the illegal website, but from the perspective of traffic monitoring devices, the client is communicating with a legitimate website, effectively disguising the traffic as legitimate.
This method is more feasible when the blocked site and the harmless site are provided by the same large service provider, such as services from a content delivery network. At this point, censors typically find it difficult to distinguish between disguised traffic and legitimate traffic, forcing them to either allow all seemingly harmless traffic or completely block traffic for that domain. Completely blocking could cause significant collateral damage.
Fake Wall (Pseudo-Wall) Attack Solutions
1. What is a Fake Wall Attack?
A fake wall attack refers to a way of attacking websites by exploiting GFW’s functions.
Hackers set up a server A in China and a server B abroad. They then modify the hosts file on server A to point the target website, such as www.xxx.com, to server B. On server B, they create a website with illegal content and bind it to the domain www.xxx.com.
This way, accessing www.xxx.com through server A will “incorrectly” redirect to the illegal website set up by the hackers, rather than the correct server for www.xxx.com.
Hackers then use packet-sending software on server A to send a large number of requests containing illegal keywords to the www.xxx.com website. This results in illegal requests that can indeed access illegal content, leading GFW to temporarily block the www.xxx.com website via TCP blocking. If hackers continue this packet-sending attack, the website will be repeatedly and temporarily banned, resulting in long-term inaccessibility.
2. How to Determine if You Are Under a Fake Wall Attack?
If your website is frequently or long-term inaccessible, and upon checking, you find that domain resolution is normal, the WEB service is normal, access from abroad is normal, the domain is not blocked or polluted, and the server’s ports 80 and 443 are inaccessible, then it is basically a fake wall attack.
Detection websites: https://www.boce.com and https://support.dnspod.cn
Use the former to check domestic access situations, whether the domain is blocked or hijacked, and if DNS is polluted. Use the latter to check if ports 80 and 443 services are normal.
3. How to Solve a Fake Wall Attack?
Through practice, this site has found the following three solutions for fake wall attacks:
Scheme One: Register the Domain and Use a Domestic Server.
Since fake wall attacks exploit GFW’s functions, the most effective method is to register the attacked domain and use a domestic server, as GFW is designed to target websites with servers abroad.
Advantages: Once and for all, absolutely effective.
Disadvantages: Registration takes a long time, especially for websites that may have some violation content, making registration difficult.
Scheme Two: DNS Intelligent Resolution + Multi-IP Servers.
This scheme requires a large number of IPs, at least 100, and a DNS that supports API, such as Alibaba Cloud Enterprise DNS. The solution can be further divided into two methods:
One is to use API for cyclic resolution, setting it to switch to a different resolved IP every minute.
The other is to use Alibaba Cloud’s global traffic management function, set up multiple resolved IP pools, and check each resolved IP every minute. If an IP is inaccessible, intelligently switch to another normal IP for resolution.
This effectively solves the fake wall problem because there are many IPs, exceeding the blocking speed.
Advantages: Fully controllable, with control in your own hands, suitable for hands-on site administrators.
Disadvantages: High cost, as DNS and a large number of IPs require payment. It also tests technical skills, as you need to develop code to call the API or set up global traffic management and intelligent resolution functions. Additionally, it is affected by DNS server cache times in various regions, so some users will inevitably be impacted.
Scheme Three: Use a Fake Wall-Resistant CDN.
Where there is demand, there is a market. Currently, there are some CDN service providers on the market that offer anti-fake wall functions.