Self-built ICP-free Anti-theft Tailscale Domestic Relay (DERP) Tutorial
Introduction to Tailscale and DERP
What is Tailscale?
Tailscale is a P2P networking tool based on Wireguard that includes various network tools. Thanks to its P2P characteristics, Tailscale can also perform intranet penetration, breaking through NAT restrictions to directly reach another host.
What is DERP?
DERP is a relay service developed by Tailscale. When the network environment makes it difficult to penetrate (such as in campus networks, mobile corporate intranets, 4G, 5G, etc.), all traffic will be relayed via DERP to the target address.
By default, Tailscale officially provides official DERP services around the continent, but due to network connectivity issues in mainland China, official DERP nodes are not provided for the mainland. To ensure the success rate of connections in mainland China, we need to self-build a DERP service to help us “punch holes”.
Installing Docker and Docker Compose
1 | bash <(curl -Ls https://docker.denlu.top/docker.sh) |
Deploying Tailscale Client in DERP Node Service (Important)
Principle
Since we are not using a domain for deployment, we cannot use the --verify-clients parameter with a domain for client verification, making it easy for others to scan and steal it, allowing them to freeload on our valuable domestic traffic. Without verification, DERP will default to forwarding all traffic that needs to be forwarded without any checks.
Simple Installation Tutorial
Official Tutorial: Tailscale Docs
- First, use the one-click script for deployment:
curl -fsSL https://tailscale.com/install.sh | sh - Perform the login operation:
tailscale login - At this point, the console will pop up a login URL; access this URL with your browser and follow the instructions to complete the installation.
Docker Image
1 | services: |
Create a new file named: docker-compose.yml
In this folder, run docker compose up -d to start the Docker.
For servers in mainland China, you can replace the ghcr link, for example, with the one from Nanjing University (replace the third line’s image)
1 | services: |
Modify Tailscale ACL Configuration to Enable Third-party DERP
- Go to the ACL editing page: Tailscale
- Add a new configuration file
1 | "derpMap": { |
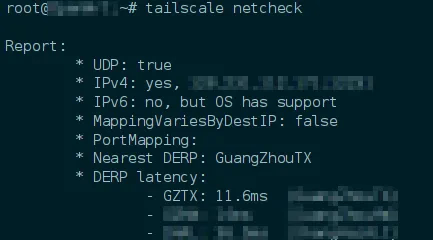
Test if Successful
Using Network Connection Test
- Find a client that is using Tailscale
- Enter the terminal
- Input
tailscale netcheck - Check if the response matches the image below
Using Ping to Test Connectivity
- Find a client that is using Tailscale
- Enter the terminal
- Input
tailscale ping your other host address - Check if it is connected (for example, if
via DER (xxx)appears, it is successful)