Hysteria2|Second Generation Hysteria Node Setup Tutorial
Hysteria2 is a feature-rich network tool optimized for harsh network environments (bidirectional acceleration), such as satellite networks, crowded public Wi-Fi, connecting to foreign servers from China, etc. Based on a modified version of the QUIC protocol.
Self-built ICP-free Anti-theft Tailscale Domestic Relay (DERP) Tutorial
By default, Tailscale officially provides DERP services around the continent, but due to network connectivity issues in mainland China, official DERP nodes are not provided for the mainland. To ensure the success rate of connections in mainland China, we need to self-build a DERP service to help us "punch holes".
A Complete Automated Anime Tracking Tutorial
Facing various ads on video platforms, I chose to set up my own platform to watch shows, which can achieve automatic anime tracking, high-definition quality, playback on all platforms, and sharing with friends. Preparation NAS or your own server ANI-RSS QB EMBY MP Autofilm (optional) qbittorrentThen establish the downloader, create a docker-compose.yml file, with the content as follows 12345678910111213141516171819202122version: "2"services: qbittorrent: image:...
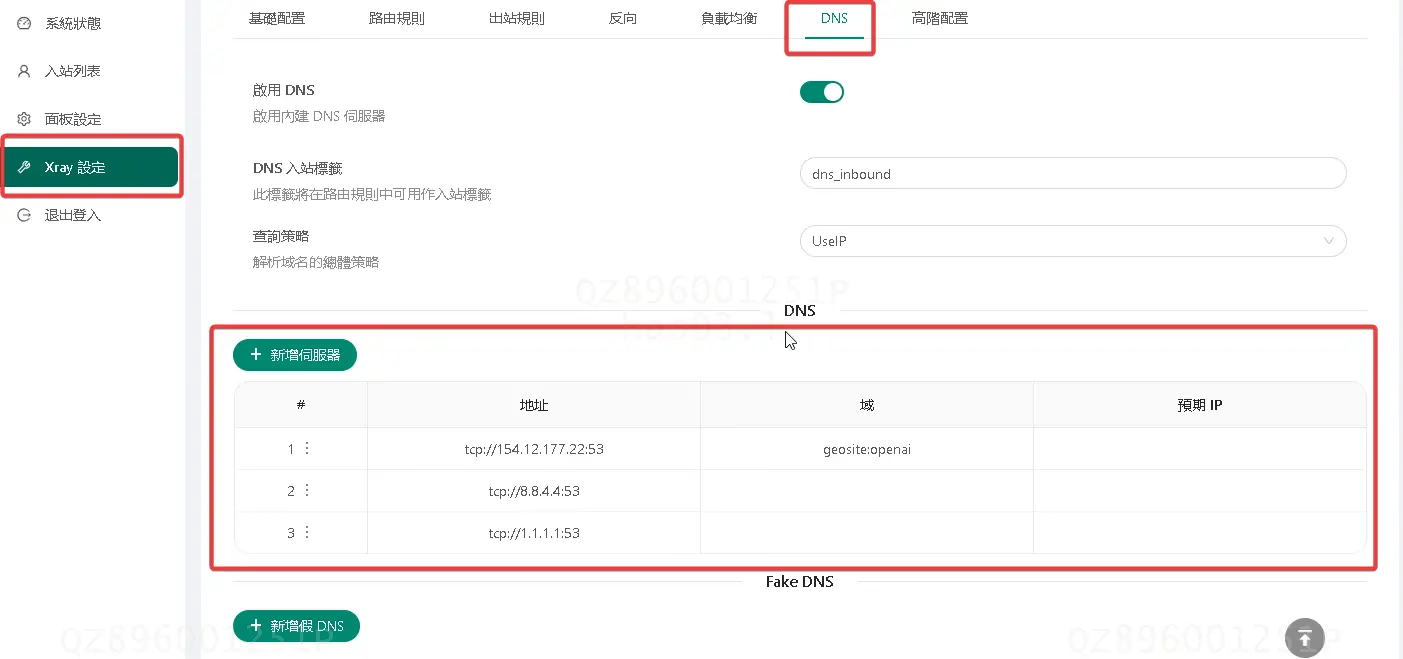
DNS Shunting to Unlock Streaming Media
First of all, thank you to the great benefactor Alice for providing free DNS service, which allows individual users to add 5 IPs for free, and can be used to unlock streaming media and AI services. v2bx Configuration for DNS Shuntingconfig.json Configuration123456789101112131415161718192021222324252627282930313233343536373839404142434445{ "Log": { "Level": "error", "Output": "" }, "Cores": [ ...
Linux Configuring Samba Service Tutorial
Installing Samba12apt updateapt install samba Configuring SambaSamba’s configuration file is usually located at /etc/samba/smb.conf. You can use a text editor (such as nano or vim) to edit this file. Add shared files. Remember to back up the file before modifying 1cp /etc/samba/smb.conf /etc/samba/smb.conf.bak 12345678[shared] comment = Shared Folder path = /home/user/shared valid users = user read only = no browsable = yes create mask = 0777 directory mask = 0777 comment:...
Methods and Fake Wall Attacks Under SNI Review
Introduction to Some Professional Terms HTTP(Hyper Text Transfer Protocol) Hypertext Transfer Protocol, used for transmitting various web pages in daily browsing, but its transmission process is not encrypted and thus insecure.What is currently referred to as supporting HTTP generally means that both HTTP and HTTPS functions can be implemented, rather than just HTTP alone. TLS(Transport Layer Security) Transport Layer Security, the successor to SSL, enables messages to be encrypted before...
One-Click DD System Network Reinstallation
AutoReinstall Script1234wget --no-check-certificate -O AutoReinstall.sh https://git.io/AutoReinstall.sh && bash AutoReinstall.sh #Version available in Chinabash <(wget --no-check-certificate -qO- https://cdn.jsdelivr.net/gh/hiCasper/Shell@master/AutoReinstall.sh) Disk Expansion After ReinstallationUse partitioning tools: Use fdisk or parted tools to delete and recreate the /dev/vda1 partition to utilize the entire disk space. For disks using a DOS partition table, here is an...
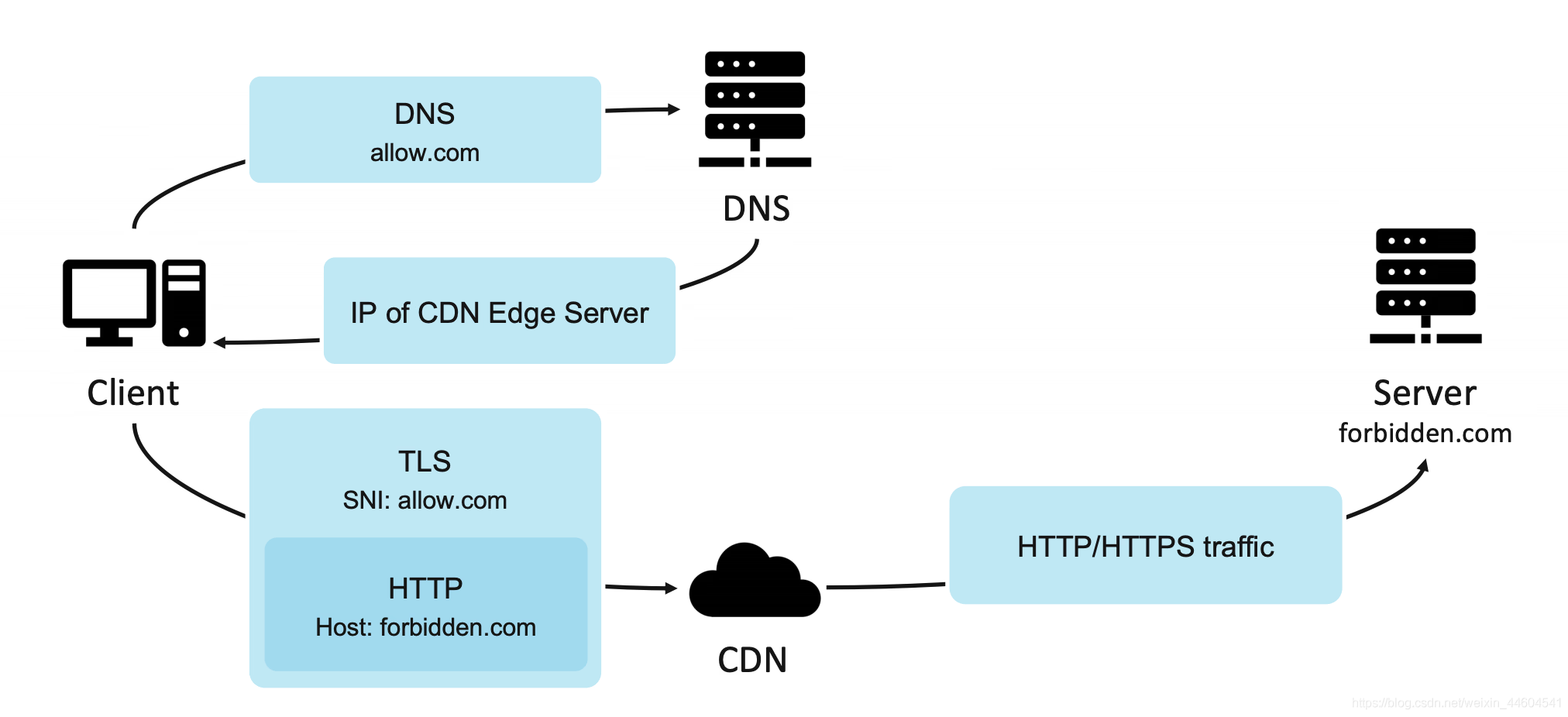
Using Unfiled Domestic Servers - Methods to Bypass SNI (HTTPS)
Simply put, the domain's port 443 is blocked, and SSL cannot access the website content. More complexly, TLS is the security foundation for network communications (HTTPS). TLS provides authentication and encryption that allows users to confirm who they are communicating with and ensures that communication information is not seen or tampered with by intermediaries. Although TLS can hide the *content* of user communications, it does not always hide the *object* of user communications. For example, the TLS handshake can carry an extension called Encrypted Server Name Indication (SNI), which helps the client tell the server the domain name of the website it wants to access. Censors, including those in China, use this extension to check and block users from accessing specific websites.
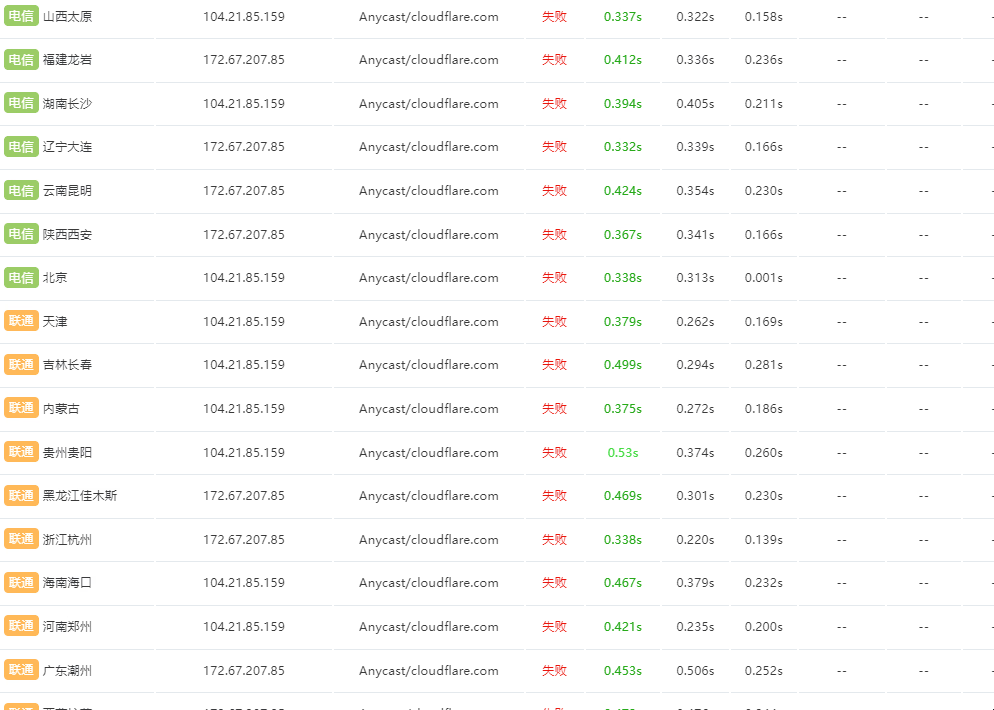
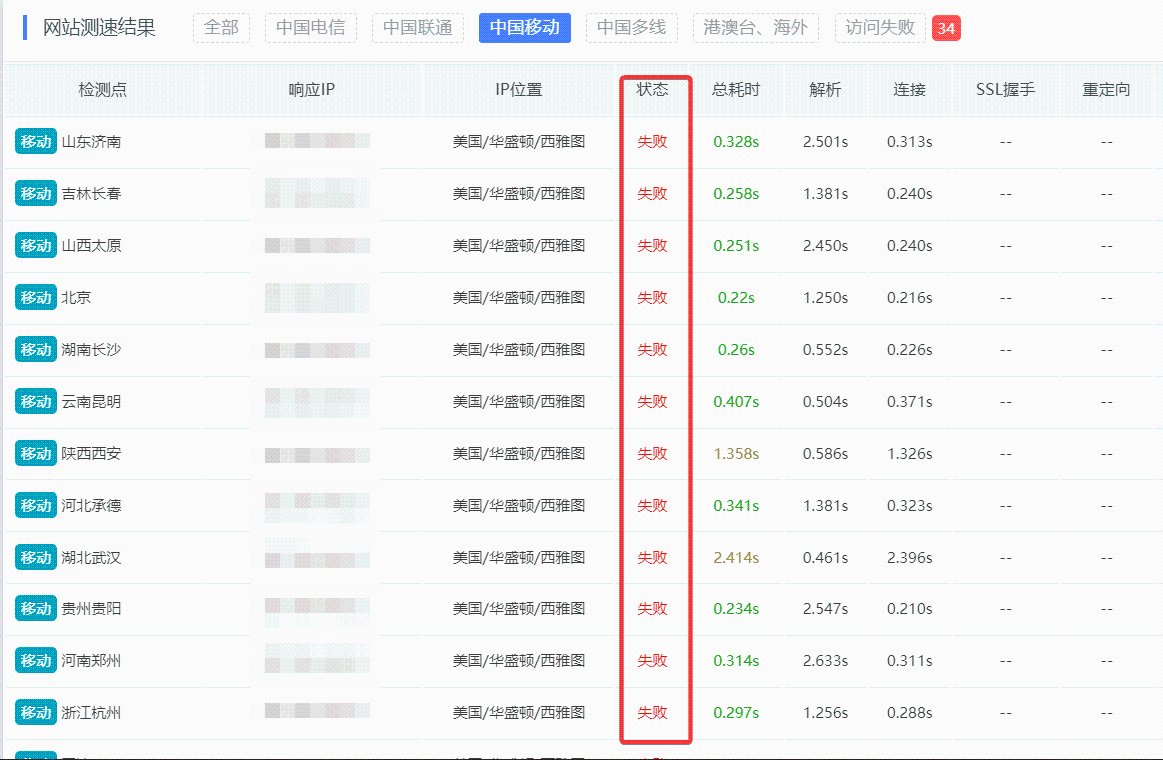
Bypassing Mobile Firewall on Domain Blocking
Some foreign servers in certain countries use fixed routes, for example, Hong Kong via Southern Telecom, Russia via Beijing Unicom; If users of China Mobile's broadband access these foreign websites, it will increase the settlement fees that China Mobile pays to Telecom and Unicom, so China Mobile will choose to directly block access, meaning the domain is walled and inaccessible.
Linux Bypass CF, Crawl Hanime Hentai Videos
Bypass CF ShieldUse cloudscraper instead of requests 1pip3 install cloudscraper 123import cloudscraperscraper = cloudscraper.create_scraper()response =scraper.get(url) Crawl Web Dynamic Content, Need to Install Selenium1pip3 install selenium 12345678910111213141516from selenium import webdriverfrom selenium.webdriver.chrome.options import Optionsurl = "xxxx"chrome_options = Options()chrome_options.add_argument('--no-sandbox') # Grant root execution...